Third-Party Fraud and the Rise of Synthetic IDs
March 31, 2022
Table Of Contents
This article is part 5 of our ongoing identity series. To read the previous blog, click here. To read part 1, click here.
What is Third-Party Fraud?
Fraud becomes more complicated the further it moves from the individual. To commit first-party fraud, all one needs to do is lie about themselves. Second-party fraud involves one other person, volunteering information for someone else to commit fraud on their behalf.
But, third-party fraud happens when someone’s identity is either stolen without their consent or knowledge (identity theft), or when an identity is fabricated altogether (synthetic ID).
This is the most common form of fraud because high-profile individuals are attractive targets for fraudsters, there’s an increase in information stored and exchanged online in a manner that is not secure, and it’s much easier for a fraudster to hide, as their own identity is not directly involved.
What are Synthetic IDs?
Synthetic IDs are partially or completely fabricated identities. They often involve some grain of truth, such as a valid social security number, paired with fabricated information to convincingly evade standard validation methods. However, fraudsters have recently been able to create manufactured identities from scratch, including social security numbers.
Synthetic IDs present a huge challenge for business, and a huge opportunity for fraudsters, because there’s often no individual victim to report the fraud. For instance, if your identity was stolen wholesale, you would quickly recognize fraudulent transactions, unexpected queries of your credit, or other fraudulent account activities that you would want to resolve as soon as possible.
But, with synthetic IDs, there is no individual victim (no you) to report the issue. Cunning fraudsters can keep accounts open for months, then close once the credit is maxed before any issues are detected.
Furthermore, fraudsters are constantly innovating. Creating a synthetic identity used to require at least some technical savvy, but today there are illicit vendors that can generate a synthetic ID at the click of a button.

The Impact of Third-Party Fraud
The cost and impact of third-party fraud is massive. According to a recent Aite-Novarica Group report, 47 percent of Americans surveyed experienced financial identity theft in 2020, and identity theft cases increased by 42% from $502.5 billion in 2019 to $712.4 billion in 2020.
Fraudsters take advantage of life changing events, such as the pandemic in 2020, where a large portion of the increase in fraud can be attributed to fraudulent identities eating into the increased and extended unemployment benefits or federal stimulus payments.
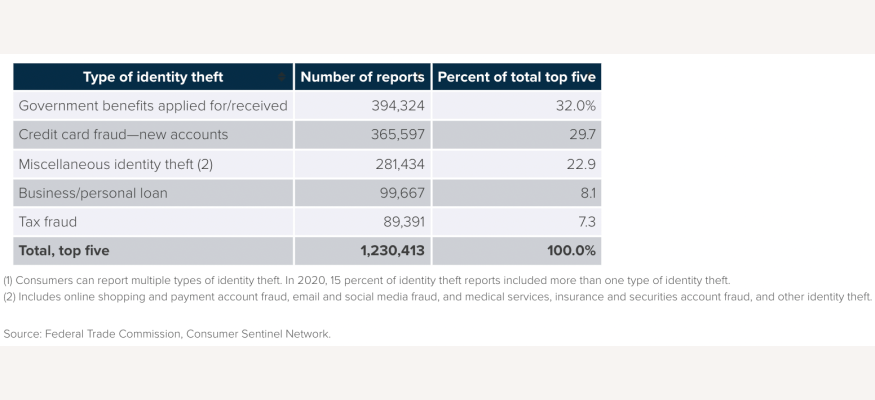
The most occurrence of third-party fraud occurs within government (32%), with credit card fraud at a close second at 29.7%, including eCommerce fraud.
How to Fight Against Third-Party Fraud and Synthetic IDs with Data
As mentioned above, regular ol’ third-party fraud is much easier to detect than synthetic IDs because there is an actual victim/identity tied to the theft. So, the best way to fight third-party fraud is to find the false instance of account creation, transaction, etc. via linkages toward other pieces of that identity. If John Doe’s new account looks legitimate except for the creator’s email being mikat727119999@mail.com instead of their email johndoe@gmail.com, that is a clear identification of fraud.
Another great data point to apply is length of time, such as how long a phone number has been operational, when social media profiles were created/last active, or how long a person has been living or working in a certain location/company. To be able to detect that, you need a clear, accurate, and secure record of people’s professional identity.
Detecting synthetic IDs requires a much more extreme, thorough utilization of data and tools to cross-reference with verified and highly protected datasets (such as valid social security numbers), and extensive resources to spot potential harm before it occurs.
If you can confidently identify the green flags, that’s a great first step. We’ve created solutions like our Identify API that allows businesses to apply necessary linkages and identify bonafide identities as quickly as possible.
Consider there are too many moving parts in third-party fraud detection for you to stop at just quality data. It’s a good thing for you to have multiple data sources. Innovative tools and platforms (like Kount, Ekata, haveibeenpwned.com, etc.) can and should tie in with a data partner to understand the situation further: metrics about devices making transactions, real-time reporting of device movement (is the device being tapped or sitting flat on a table), IP addresses, breach exposure, etc.
Connecting identifiable information from a data partner like PDL to potential attack vectors from third-party data sources can inform you on what is worthwhile to pay attention to for your business. Conversely, the effectiveness of these tools is highly reliant on the quality of the data pipelined into these platforms.
Ready to get started or have questions? Reach out to our team today for a free consultation.
Like what you read? Scroll down and subscribe to our newsletter to receive monthly updates with our latest content.